Play Ransomware in 2023: Strategic marketing for an emerging digital threat
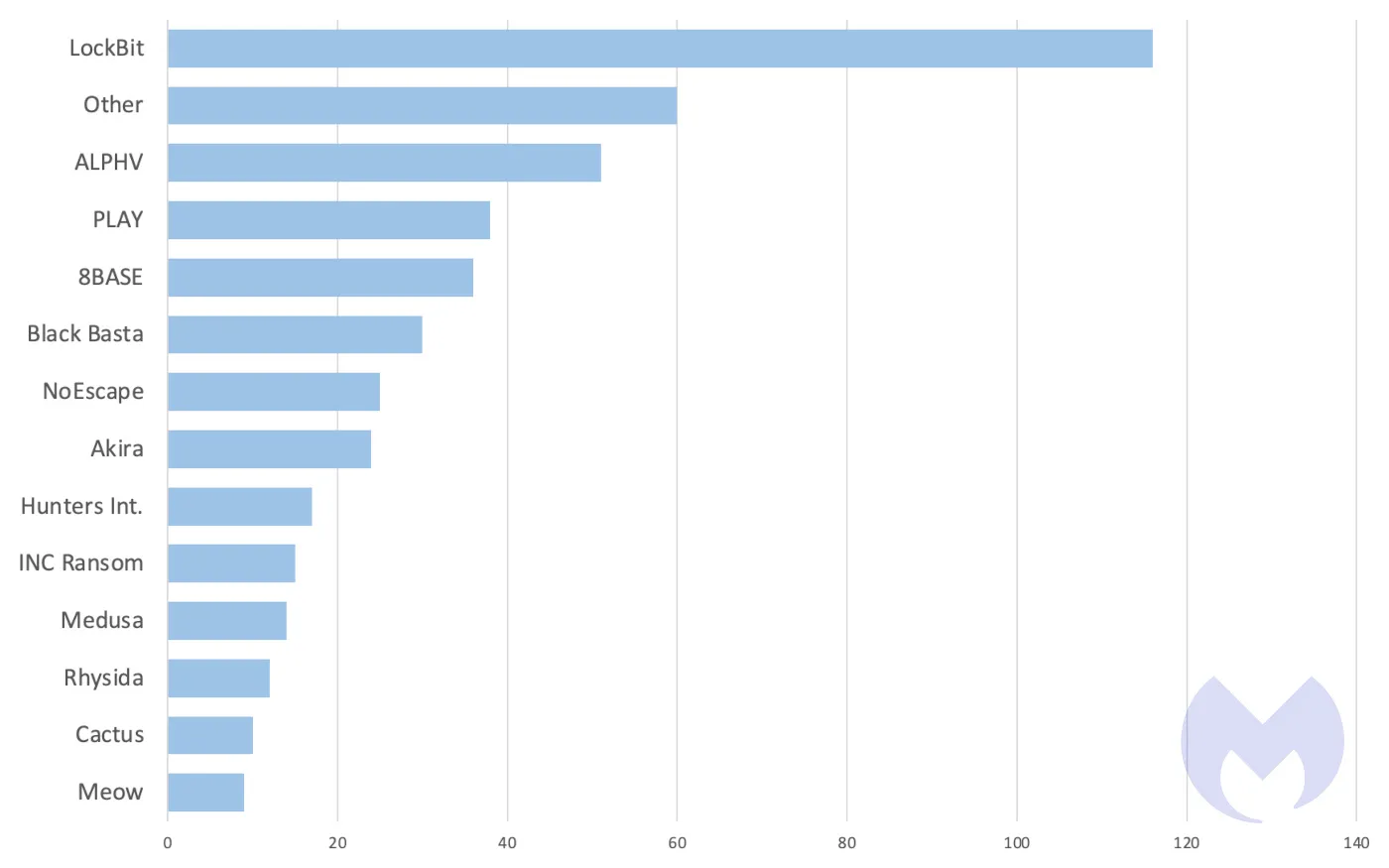
In an ever-evolving digital landscape, cybersecurity emerges as an unavoidable priority. Within this realm of perpetual challenges, the ransomware entity known as Play has undergone a substantial evolution, embracing double extortion tactics and commercializing its operations. Also recognized as Balloonfly and PlayCrypt, this ransomware made its initial debut in June 2022, exploiting targeted vulnerabilities within Microsoft Exchange Server, such as (CVE-2022-41040 and CVE-2022-41082). These vulnerabilities enable server-side request forgery (SSRF) and remote code execution when the attacker gains access to Microsoft Exchange through PowerShell. This group attains initial access to victims’ networks by exploiting valid accounts (T1078) and abusing public applications (T1190), specifically targeting vulnerabilities in FortiOS (CVE-2018-13379 and CVE-2020-12812) and Microsoft Exchange (ProxyNotShell [CVE-2022-41040 and CVE-2022-41082]). Play ransomware actors have been observed employing external services (T1133), such as Remote Desktop Protocol (RDP) and Virtual Private Networks (VPN), for their initial access strategies. Play has embraced the alarming trend of Ransomware as a Service (RaaS), facilitating other cybercriminals in launching their own campaigns using Play Ransomware’s infrastructure and tactics. This approach allows individuals to execute attacks with ease, following detailed instructions provided as part of the service. One of the most noteworthy findings emphasized in the report issued by Adlumin is the notable lack of diversity among Play ransomware attacks. This uniformity spans various aspects, ranging from the consistent selection of public music folders to conceal malicious files to the utilization of identical passwords for creating accounts with elevated privileges. Play ransomware actors employ a double extortion model, encrypting systems only after extracting sensitive data. Notably, the ransom notes do not contain an initial ransom demand or payment instructions. Instead, victims are directed to initiate contact with the threat actors through email for further communication and negotiation. The adoption of this tactic amplifies the pressure on victims and broadens the potential for success for malicious operators. According to statistics compiled by Malwarebytes, Play Ransomware left its mark on nearly 40 victims in November 2023 alone, ranking just behind LockBit and BlackCat (also known as ALPHV and Noberus). In light of this sophisticated evolution, organizations must implement robust preventive measures. Some of the mitigation measures recommended by the FBI, CISA, and ASD’s ACSC include: For more information about the tactics, techniques and procedures (TTP) of the Play ransomware group: https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-352a Author: Reynaldo C. de la Fuente. Partner Director Play Ransomware in 2023: Strategic marketing for an emerging digital threat
December 22, 2023.